A) Junos Fusion Provider Edge
B) Virtual Chassis
C) Junos Fusion Data Center
D) Virtual Chassis Fabric
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are seeking a server-virtualization security solution that is lightweight and will protect virtual machines from a variety of threats. Which platform should you choose in this scenario?
A) vSRX
B) vRR
C) vEPC
D) TCX
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You want to provide Layer 2 connectivity to a backup data center or to a disaster recovery site. What would you use to accomplish this task?
A) Data Center Interconnect
B) network redundancy
C) SDN
D) SAN protocols
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Your data center uses an Ethernet fabric solution for the infrastructure switches. You must design a redundancy solution that addresses how the servers connect to the members of the Ethernet fabric. Which two statements are true in this scenario? (Choose two.)
A) It is necessary to use MC-LAG.
B) You should connect each server to one member with a two-interface LAG.
C) You should connect each server to two different members.
D) It is not necessary to use MC-LAG.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Click the Exhibit button. Traffic congestion is noticed when sending traffic from S1 to S2. You must design a CoS deployment to address the traffic congestion issue. Referring to the exhibit, which two statements are true? (Choose two.) 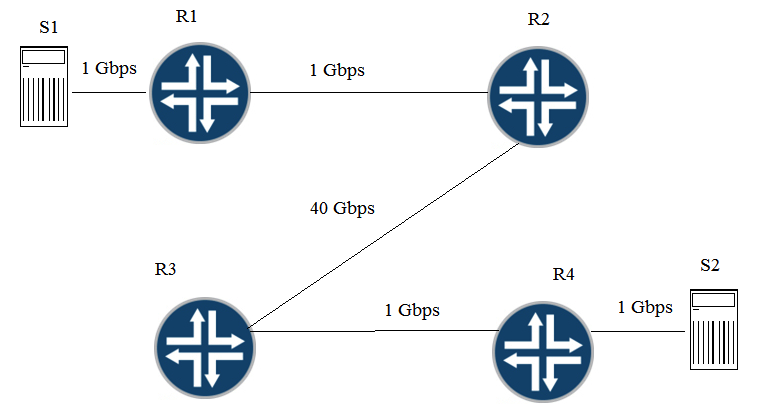
A) You should use BA classifiers on R1.
B) You should use multifield classifiers on R2, R3, and R4.
C) You should use multifield classifiers on R1.
D) You should use BA classifiers on R2, R3, and R4.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are designing a Layer 2 fabric implementation for a small data center and have chosen to implement a Virtual Chassis Fabric. You must accommodate two racks of servers with 1 Gbps connectivity, 10 racks of servers with 10 Gbps connectivity, and maintain a single management interface. Which device would satisfy the requirements in this implementation?
A) QFX5110
B) QFX10002
C) EX4600
D) EX4300
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Your data center uses a Virtual Chassis Fabric. The ToR switches have 48 ports and each rack supports 20 servers. Each server has two ports that are configured as a LAG. You need to implement link level redundancy but you cannot use two ports on the same device for this redundancy. Which type of connection should you use to complete this task?
A) MC-LAG
B) RTG
C) LAG
D) ESI
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Your data center uses a Virtual Chassis Fabric. The ToR switches have 48 ports and each rack supports 20 servers. Each server has two ports that are configured as a LAG. You need to implement link level redundancy but you cannot use two ports on the same device for this redundancy. Which type of connection should you use to complete this task?
A) MC-LAG
B) RTG
C) LAG
D) ESI
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are designing a data center network with a combination of KVM virtual machines and physical QFX Series devices. You require a single Juniper Networks solution for monitoring resource utilization across all devices. In this scenario, which product would satisfy this requirement?
A) AppFormix
B) Contrail
C) JTI
D) Junos Space
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are designing a DCI strategy. You must provide a solution that meets the requirements shown below: -sub 50 ms failover to alternate path -supports L2 and L3 VPNs -supports traffic engineered paths Which technology would satisfy the requirements?
A) MPLS
B) GRE
C) BGP
D) IPsec
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
How many inches does one RU equal?
A) 1.000
B) 1.251
C) 1.527
D) 1.752
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which protocol is used on the VPCs of a Virtual Chassis Fabric?
A) IEEE 802.1BR
B) MPLS
C) VCCP
D) IS-IS
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are designing a Layer 2 fabric implementation for a small data center and have chosen to implement a Virtual Chassis Fabric. You must accommodate two racks of servers with 1 Gbps connectivity, 10 racks of servers with 10 Gbps connectivity, and maintain a single management interface. Which device would satisfy the requirements in this implementation?
A) QFX5110
B) QFX10002
C) EX4600
D) EX4300
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You plan to deploy a set of SRX Series devices in an active/active chassis cluster with an active/active network infrastructure. Which two statements are true in this scenario? (Choose two.)
A) This deployment scenario is recommended when firewall services are used extensively for east-west traffic.
B) End-host traffic is services through one SRX node during non-failure conditions.
C) This deployment scenario is recommended when firewall services are used extensively for north-south traffic.
D) End-host traffic is serviced through both SRX nodes during non-failure conditions.
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What are two methods used to protect the data center perimeter? (Choose two.)
A) session authentication
B) DDoS protection
C) asset classification
D) network subnetting
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which two statements are correct about current data center designs? (Choose two.)
A) Network functions are being virtualized.
B) Public IP addresses are easy to obtain but not manage.
C) There is a proliferation of distributed applications.
D) There is a proliferation of monolithic applications.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are implementing a Virtual Chassis Fabric using QFX5110 devices. Which two statements are true in this scenario according to Juniper Networks recommendations? (Choose two.)
A) Spine devices must assume the RE role.
B) Leaf devices must have a direct link to all other leaf devices.
C) Spine devices must assume the line card role.
D) Leaf devices must have a direct link to all spine devices.
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Click the Exhibit button. Traffic congestion has been noticed when S1 is sending traffic to S2. You must design a CoS deployment to address the traffic congestion issue. Referring to the exhibit, which statement is true? 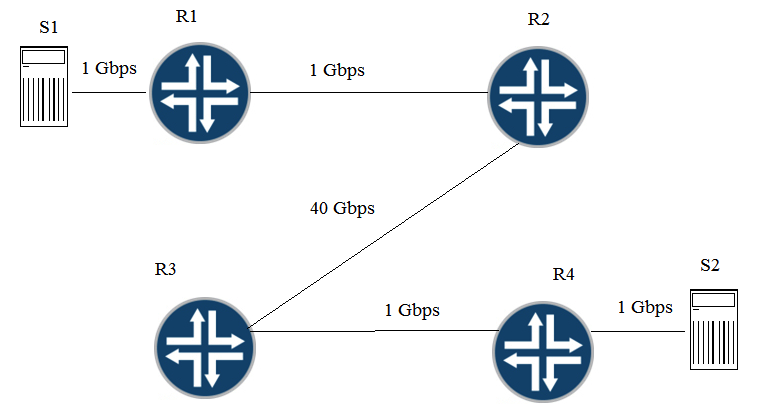
A) You should deploy CoS on R1 and R4.
B) You should deploy CoS on R1, R3 and R4.
C) You should deploy CoS on S1, R1, R2, R3, R4, and S2.
D) You should deploy CoS on R1, R2, R3, and R4.
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You want to use the Intrusion Prevention System features of a vSRX virtual firewall to protect systems from attacks embedded in traffic. In this scenario, which three technologies would be used? (Choose three.)
A) protocol decodes
B) zero-day protection
C) traffic normalization
D) application firewall
E) application tracking
G) D) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are asked to create a new data center based on an IP fabric architecture. The data center must support many segmented applications that require Layer 2 adjacencies. You decide to use EVPN-VXLAN as an overlay technology to accomplish the task. To meet the requirements, each application will be placed in its own VLAN. In this scenario, what is required for communication between VLANs to occur?
A) IBGP and Q-in-Q
B) IBGP and MP-BGP
C) IBGP and MPLS
D) IBGP and GVRP
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Showing 21 - 40 of 74
Related Exams