A) Antivirus
B) Patch management
C) Log monitoring
D) Application whitelisting
E) Awareness training
G) B) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is the GREATEST security concern with respect to BYOD?
A) The filtering of sensitive data out of data flows at geographic boundaries.
B) Removing potential bottlenecks in data transmission paths.
C) The transfer of corporate data onto mobile corporate devices.
D) The migration of data into and out of the network in an uncontrolled manner.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An organization is struggling to differentiate threats from normal traffic and access to systems. A security engineer has been asked to recommend a system that will aggregate data and provide metrics that will assist in identifying malicious actors or other anomalous activity throughout the environment. Which of the following solutions should the engineer recommend?
A) Web application firewall
B) SIEM
C) IPS
D) UTM
E) File integrity monitor
G) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An organization is currently performing a market scan for managed security services and EDR capability. Which of the following business documents should be released to the prospective vendors in the first step of the process? (Select TWO) .
A) MSA
B) RFP
C) NDA
D) RFI
E) MOU
F) RFQ
H) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
During a security assessment, activities were divided into two phases: internal and external exploitation. The security assessment team set a hard time limit on external activities before moving to a compromised box within the enterprise perimeter. Which of the following methods is the assessment team most likely to employ NEXT?
A) Pivoting from the compromised, moving laterally through the enterprise, and trying to exfiltrate data and compromise devices.
B) Conducting a social engineering attack attempt with the goal of accessing the compromised box physically.
C) Exfiltrating network scans from the compromised box as a precursor to social media reconnaissance
D) Open-source intelligence gathering to identify the network perimeter and scope to enable further system compromises.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A financial institution would like to store its customer data in a cloud but still allow the data to be accessed and manipulated while encrypted. Doing so would prevent the cloud service provider from being able to decipher the data due to its sensitivity. The financial institution is not concerned about computational overheads and slow speeds. Which of the following cryptographic techniques would BEST meet the requirement?
A) Asymmetric
B) Symmetric
C) Homomorphic
D) Ephemeral
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
During the deployment of a new system, the implementation team determines that APIs used to integrate the new system with a legacy system are not functioning properly. Further investigation shows there is a misconfigured encryption algorithm used to secure data transfers between systems. Which of the following should the project manager use to determine the source of the defined algorithm in use?
A) Code repositories
B) Security requirements traceability matrix
C) Software development lifecycle
D) Roles matrix
E) Implementation guide
G) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A systems administrator at a medical imaging company discovers protected health information (PHI) on a general-purpose file server. Which of the following steps should the administrator take NEXT?
A) Isolate all of the PHI on its own VLAN and keep it segregated at Layer 2
B) Immediately encrypt all PHI with AES-256
C) Delete all PHI from the network until the legal department is consulted
D) Consult the legal department to determine legal requirements
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A Chief Information Security Officer (CISO) is running a test to evaluate the security of the corporate network and attached devices. Which of the following components should be executed by an outside vendor?
A) Penetration tests
B) Vulnerability assessment
C) Tabletop exercises
D) Blue-team operations
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A medical facility wants to purchase mobile devices for doctors and nurses. To ensure accountability, each individual will be assigned a separate mobile device. Additionally, to protect patients' health information, management has identified the following requirements: Data must be encrypted at rest. The device must be disabled if it leaves the facility. The device must be disabled when tampered with. Which of the following technologies would BEST support these requirements? (Select two.)
A) eFuse
B) NFC
C) GPS
D) Biometric
E) USB 4.1
F) MicroSD
H) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A security engineer is embedded with a development team to ensure security is built into products being developed. The security engineer wants to ensure developers are not blocked by a large number of security requirements applied at specific schedule points. Which of the following solutions BEST meets the engineer's goal?
A) Schedule weekly reviews of al unit test results with the entire development team and follow up between meetings with surprise code inspections.
B) Develop and implement a set of automated security tests to be installed on each development team leader's workstation.
C) Enforce code quality and reuse standards into the requirements definition phase of the waterfall development process.
D) Deploy an integrated software tool that builds and tests each portion of code committed by developers and provides feedback.
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Within the past six months, a company has experienced a series of attacks directed at various collaboration tools. Additionally, sensitive information was compromised during a recent security breach of a remote access session from an unsecure site. As a result, the company is requiring all collaboration tools to comply with the following: Secure messaging between internal users using digital signatures Secure sites for video-conferencing sessions Presence information for all office employees Restriction of certain types of messages to be allowed into the network. Which of the following applications must be configured to meet the new requirements? (Choose two.)
A) Remote desktop
B) VoIP
C) Remote assistance
D) Email
E) Instant messaging
F) Social media websites
H) C) and F)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A security researcher is gathering information about a recent spoke in the number of targeted attacks against multinational banks. The spike is on top of already sustained attacks against the banks. Some of the previous attacks have resulted in the loss of sensitive data, but as of yet the attackers have not successfully stolen any funds. Based on the information available to the researcher, which of the following is the MOST likely threat profile?
A) Nation-state-sponsored attackers conducting espionage for strategic gain.
B) Insiders seeking to gain access to funds for illicit purposes.
C) Opportunists seeking notoriety and fame for personal gain.
D) Hacktivists seeking to make a political statement because of socio-economic factors.
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
At a meeting, the systems administrator states the security controls a company wishes to implement seem excessive, since all of the information on the company's web servers can be obtained publicly and is not proprietary in any way. The next day the company's website is defaced as part of an SQL injection attack, and the company receives press inquiries about the message the attackers displayed on the website. Which of the following is the FIRST action the company should take?
A) Refer to and follow procedures from the company's incident response plan.
B) Call a press conference to explain that the company has been hacked.
C) Establish chain of custody for all systems to which the systems administrator has access.
D) Conduct a detailed forensic analysis of the compromised system.
E) Inform the communications and marketing department of the attack details.
G) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A penetration tester has been contracted to conduct a physical assessment of a site. Which of the following is the MOST plausible method of social engineering to be conducted during this engagement?
A) Randomly calling customer employees and posing as a help desk technician requiring user password to resolve issues
B) Posing as a copier service technician and indicating the equipment had "phoned home" to alert the technician for a service call
C) Simulating an illness while at a client location for a sales call and then recovering once listening devices are installed
D) Obtaining fake government credentials and impersonating law enforcement to gain access to a company facility
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A vulnerability was recently announced that allows a malicious user to gain root privileges on other virtual machines running within the same hardware cluster. Customers of which of the following cloud-based solutions should be MOST concerned about this vulnerability?
A) Single-tenant private cloud
B) Multitenant SaaS cloud
C) Single-tenant hybrid cloud
D) Multitenant IaaS cloud
E) Multitenant PaaS cloud
F) Single-tenant public cloud
H) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A secure facility has a server room that currently is controlled by a simple lock and key, and several administrators have copies of the key. To maintain regulatory compliance, a second lock, which is controlled by an application on the administrators' smartphones, is purchased and installed. The application has various authentication methods that can be used. The criteria for choosing the most appropriate method are: It cannot be invasive to the end user. It must be utilized as a second factor. Information sharing must be avoided. It must have a low false acceptance rate. Which of the following BEST meets the criteria?
A) Facial recognition
B) Swipe pattern
C) Fingerprint scanning
D) Complex passcode
E) Token card
G) C) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A systems administrator recently joined an organization and has been asked to perform a security assessment of controls on the organization's file servers, which contain client data from a number of sensitive systems. The administrator needs to compare documented access requirements to the access implemented within the file system. Which of the following is MOST likely to be reviewed during the assessment? (Choose two.)
A) Access control list
B) Security requirements traceability matrix
C) Data owner matrix
D) Roles matrix
E) Data design document
F) Data access policies
H) B) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Click on the exhibit buttons to view the four messages. 
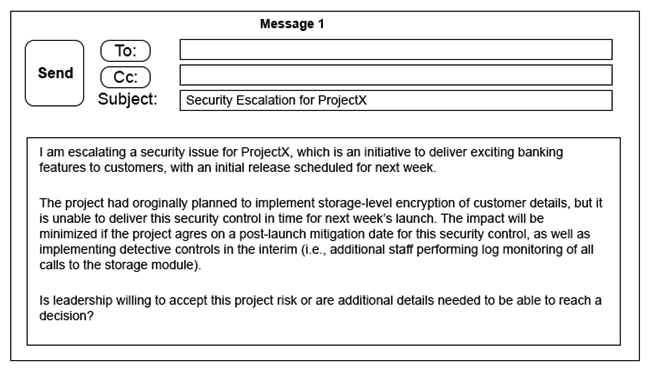
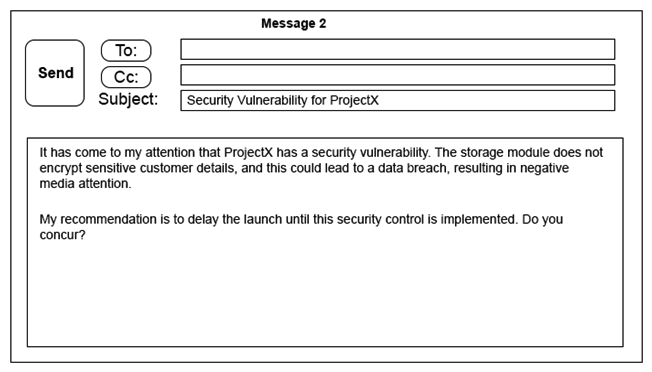
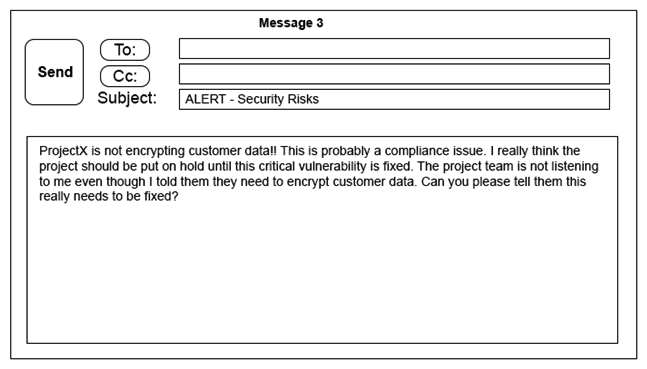
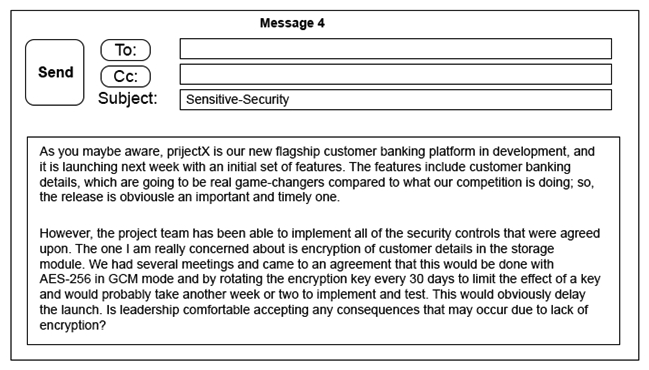 A security architect is working with a project team to deliver an important service that stores and processes customer banking details. The project, internally known as ProjectX, is due to launch its first set of features publicly within a week, but the team has not been able to implement encryption-at-rest of the customer records. The security architect is drafting an escalation email to senior leadership. Which of the following BEST conveys the business impact for senior leadership?
A security architect is working with a project team to deliver an important service that stores and processes customer banking details. The project, internally known as ProjectX, is due to launch its first set of features publicly within a week, but the team has not been able to implement encryption-at-rest of the customer records. The security architect is drafting an escalation email to senior leadership. Which of the following BEST conveys the business impact for senior leadership?
A) Message 1
B) Message 2
C) Message 3
D) Message 4
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A security appliance vendor is reviewing an RFP that is requesting solutions for the defense of a set of web-based applications. This RFP is from a financial institution with very strict performance requirements. The vendor would like to respond with its solutions. Before responding, which of the following factors is MOST likely to have an adverse effect on the vendor's qualifications?
A) The solution employs threat information-sharing capabilities using a proprietary data model.
B) The RFP is issued by a financial institution that is headquartered outside of the vendor's own country.
C) The overall solution proposed by the vendor comes in less that the TCO parameter in the RFP.
D) The vendor's proposed solution operates below the KPPs indicated in the RFP.
F) None of the above
Correct Answer

verified
Correct Answer
verified
Showing 101 - 120 of 442
Related Exams